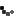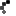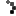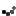Internet Information Services (IIS) 10 Request Filtering is a powerful feature that enhances the security and performance of web applications. By providing a robust mechanism for controlling the types of HTTP requests processed by the server, Request Filtering helps safeguard web applications against various threats, such as SQL injection, cross-site scripting (XSS), and other common exploits. This feature allows administrators to define rules that restrict or block potentially harmful requests based on specific criteria, such as URL length, file extensions, or query strings. Additionally, Request Filtering can improve server performance by preventing the processing of unnecessary or malicious requests, thereby optimizing resource utilization. Overall, IIS 10 Request Filtering is an essential tool for maintaining a secure and efficient web environment.
Installing IIS 10 Request Filtering
Within IIS Manager you can you can access Request Filtering at the server level or site level. If you configure it at the server level then it will apply to all sites configured on your server. Conversely if you apply it at the site level it will only apply to that specific site.
If you do not see Request Filtering in IIS Manager just go back to Server Manager and select it from Add Roles And Features. It is under the Web Server Role Security features.
IIS 10 Request Filtering Unlisted File Extensions
By default IIS 10 Request Filtering has a lot already configured but you may be included to go even further. I was recently working on an application issue where the server had the Allow unlisted file extensions setting disabled. This means all file extensions required by the application had to be specifically listed. In this case none of the good file extensions had been listed so the site was broken.
As you can see in the error below, Request Filtering is blocking the files from loading.
For even more error details you could also enable Failed Request Tracing. That too has to be added as a Role feature from Server Manager if you haven’t already added it.
Finding file extensions
Naturally the first thing to do before enabling this particular security feature is to identify which file extensions are used by application. You can do this several ways. Here’s an example using Python.
import os def list_file_extensions(folder_path): # Set to store unique file extensions extensions = set() # Walk through the directory for root, dirs, files in os.walk(folder_path): for file in files: # Get the extension of the file extension = os.path.splitext(file)[1] if extension: # Ensure it's not an empty string extensions.add(extension) # Print each unique extension found for ext in sorted(extensions): print(ext) # Specify the path to the folder folder_path = '/path/to/your/folder' list_file_extensions(folder_path)
Here’s an example using powershell
#Define the path to the directory $directoryPath = "C:\Path\To\Your\Folder" # Get all files in the directory $files = Get-ChildItem -Path $directoryPath -Recurse -File # Extract the extensions and remove duplicates $extensions = $files | Select-Object -ExpandProperty Extension -Unique # Output the unique extensions $extensions
From the script output you can see my test site has quite a few file extensions that need to be added to the allow list.
IIS 10 Request Filtering Allow File Extensions
Adding file extensions to be allowed by Request Filtering is a simple matter of clicking Allow File Name Extension.
Alternatively if you have a lot of files you can add them in bulk using the applicationHost.config file. Be sure to back that up first before making any changes.
After adding the file extensions used by the application I was still getting an error. It turned out that I needed to add a period “.” as an allowed file extension and then everything worked as expected.
In Summary
In conclusion, leveraging IIS 10 Request Filtering is a powerful option for increasing the security of your web applications. By carefully controlling the types of HTTP requests that your server processes, you can effectively mitigate a wide array of security threats, ensuring a safer online environment for both your users and your data. However, it is essential to approach the implementation of Request Filtering with caution. Thorough testing in a sandbox environment is a must to identify any potential impact on legitimate traffic and to fine-tune the filtering rules accordingly. This careful approach will help you strike the right balance between enhanced security and uninterrupted user experience, ultimately leading to a more robust and reliable web application.